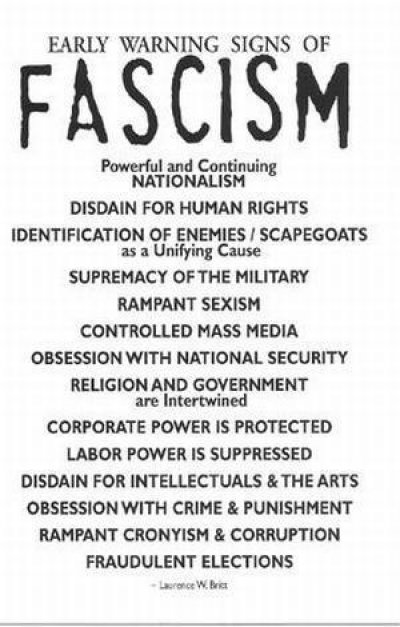
Introduction
by David Ratcliffe
This set of materials focuses on how the ideals of America—that of being a civilian republic—were transformed during the 20th century into the national security state structure that began operating after World War II. This transformation resulted in the assassination politics that defined the 1960s and continues expanding its influence with each passing year. A useful definition of seven characteristics of a national security state from SourceWatch begins with, “The National Security State or Doctrine, generally refers to the ideology and institutions (CIA, Dept. of Defense) established by the National Security Act of 1947…”[1]
The seminal event in the overt inauguration of our national security state was the assassination of the 35th President of the United States on 22 November 1963. The origination of JFK’s extra-constitutional firing was the establishment 16 years earlier of the covert doctrine of “plausible deniability” which codified criminal acts including assassination.
“Plausible deniability” was sanctioned by the June 18, 1948, National Security Council directive NSC 10/2. “Since NSC 10/2 authorized violations of international law, it also established official lying as their indispensable cover. All such activities had to be ‘so planned and executed that any US government responsibility for them is not evident to unauthorized persons, and that if uncovered the US government can plausibly deny any responsibility for them.’”[2]
In time, National Security Council Directive 10/2 and its descendant, NSC 5412, also known as the Special Group 5412/2, a subcommittee of the National Security Council, was employed by Allen Dulles to develop and operate clandestine operations world-wide.[3]
A democracy within a national security state cannot survive. [President Truman’s] decision to base our security on nuclear weapons created the contradiction of a democracy ruled by the dictates of the Pentagon. A democratic national security state is a contradiction in terms.
The insecure basis of our security then became weapons that could destroy the planet. To protect the security of that illusory means of security, which was absolute destructive power, we now needed a ruling elite of national security managers with an authority above that of our elected representatives.[4]
[1] SourceWatch is a wiki published by the Center for Media and Democracy. For additional background, see: “In The Context of Its Time: The National Security Act of 1947,” from Understanding Special Operations And Their Impact on The Vietnam War Era; 1989 Interview with L. Fletcher Prouty Colonel USAF (Retired) (rat haus reality press, 1999).
[2] Peter Grose, Gentleman Spy: The Life of Allen Dulles (New York: Houghton Mifflin, 1994), p. 293. See a description of the Special Group 10/2 and its descendant, the Special Group 5412 or 5412/2, by Col. L. Fletcher Prouty (USAF, ret.) in href=”http://www.ratical.org/ratville/JFK/40Comm.html”>“The Forty Committee,” Genesis, February, 1975, pp. 28, 105-108; and “Appendix C, NSC 5412, ‘National Security Council Directive on Covert Operations’,” from Understanding Special Operations, pp. 330-32. See also: Document 292. National Security Council Directive on Office of Special Projects – NSC 10/2 from Foreign Relations of the United States, 1945-1950, Retrospective Volume, Emergence of the Intelligence Establishment, (Washington: U.S. Government Printing Office, 1996).
[4] Quote from “Jim Douglass on The Hope in Confronting the Unspeakable in the Assassination of President John Fitzgerald Kennedy,” Keynote Address at The Coalition on Political Assassinations Conference, 20 November 2009, Dallas, Texas.
The National Security State or Doctrine, generally refers to the ideology and institutions (CIA, Dept. of Defense) established by the National Security Act of 1947[1], an enduring legacy of then President Harry S. Truman, in support of his doctrine [2] “to support free peoples who are resisting attempted subjugation by armed minorities or by outside pressures.” (Ref. Michael J. Hogan, A Cross of Iron: Harry S. Truman and the Origins of the National Security State, 1945-1954. New York: Cambridge University Press, 1998; which “explains the transformative process that ended in the ultimate demise of the New Deal state with its emphasis on social spending and ushered in the militarist National Security State.”) [3]
In his book “Brave New World Order” (Orbis Books, 1992, paper), Jack Nelson-Pallmeyer identified seven characteristics of a National Security State [4]:
The first characteristic of a National Security State is that the military is the highest authority. In a National Security State the military not only guarantees the security of the state against all internal and external enemies, it has enough power to determine the overall direction of the society. In a National Security State the military exerts important influence over political, economic, as well as military affairs.
A second defining feature of a National Security State is that political democracy and democratic elections are viewed with suspicion, contempt, or in terms of political expediency. National Security States often maintain an appearance of democracy. However, ultimate power rests with the military or within a broader National Security Establishment.
A third characteristic of a National Security State is that the military and related sectors wield substantial political and economic power. They do so in the context of an ideology which stresses that ‘freedom” and “development” are possible only when capital is concentrated in the hands of elites.
A fourth feature of a National Security State is its obsession with enemies. There are enemies of the state everywhere. Defending against external and/or internal enemies becomes a leading preoccupation of the state, a distorting factor in the economy, and a major source of national identity and purpose.
A fifth ideological foundation of a National Security State is that the enemies of the state are cunning and ruthless. Therefore, any means used to destroy or control these enemies is justified.
A sixth characteristic of a National Security State is that it restricts public debate and limits popular participation through secrecy or intimidation. Authentic democracy depends on participation of the people. National Security States limit such participation in a number of ways: They sow fear and thereby narrow the range of public debate; they restrict and distort information; and they define policies in secret and implement those policies through covert channels and clandestine activities. The state justifies such actions through rhetorical pleas of “higher purpose” and vague appeals to “national security.”
Finally, the church is expected to mobilize its financial, ideological, and theological resources in service to the National Security State.
Books
Michael H. Hogan, A Cross of Iron: Harry S Truman and the Origins of the National Security State, 1945-1954, Cambridge University Press, 1998. ISBN 0521795370 ISBN 978-0521795371
Related SourceWatch Resources
military-industrial complex
national security
National Security and Homeland Security Presidential Directive
New World Order
open government
preemptive war
The CIA and journalism
State of national emergency
state secrets privilege
Truman doctrine
homeland detention
National Security Strategy
FEDERATION OF AMERICAN SCIENTISTS INTELLIGENCE RESOURCE PROGRAM
FEDERATION OF AMERICAN SCIENTISTS
Listen to the author at http://www.expertwitnessradio.org
HIGHLY RECOMMENDED:
WHOWHATWHY DOCUMENTARY COUNTER-INTELLIGENCE: PART 1 THE COMPANY
WHOWHATWHY DOCUMENTARY COUNTER-INTELLIGENCE: PART 2 THE DEEP STATE
FROM PSYWAR:
RACHEL MADDOW EXPLAINS HOW THE FBI CAN ASSASSINATE ANYONE
INTERVIEW WITH MICHAEL HASTINGS ON “THE OPERATORS”
FRIEND OF MICHAEL HASTINGS SAYS HE WAS WORKING ON BIGGEST STORY YET ON CIA
CIA Director Brennan Confirmed as Reporter Michael Hastings Next Target
Posted on14 August 2013.
NOVANEWS
● This week Elise Jordan, wife of famed journalist Michael Hastings, who recently died under suspicious circumstances, corroborated this reporter’s sources that CIA Director, John Brennan was Hastings next exposé project (CNN clip).
● Last month a source provided San Diego 6 News with an alarming email hacked from super secret CIA contractor Stratfor’s President Fred Burton. The email (link here) was posted on WikiLeaks and alleged that then Obama counter-terrorism Czar Brennan, was in charge of the government’s continued crackdown or witch-hunt on investigative journalists.
● An SDSU professor Morteza M. Mehrabadi, Professor and Interim Chair Areas of Specialization: Mechanics of Materials told San Diego 6 News that calculating the speed of Hastings car follows a simple mathematic equation. By using the video and the distance traveled (195 feet) as well as the seconds that lapsed prior to the explosion – in his opinion, the car was traveling roughly 35 mph.
● That revelation is important because Jose, an employee of ALSCO a nearby business, and a witness to the accident told KTLA/Loud Labs (Scott Lane) the car was traveling at a high rate of speed and he saw sparks coming from the car and saw it explode BEFORE hitting the tree. The pre-explosion could possibly explain the flash of light on the video that preceded the appearance of the car in the video.
On Monday February 27th, 2012, WikiLeaks began publishing The Global Intelligence Files, over five million e-mails from the Texas headquartered “global intelligence” company Stratfor. The e-mails date between July 2004 and late December 2011. They reveal the inner workings of a company that fronts as an intelligence publisher, but provides confidential intelligence services to large corporations, such as Bhopal’s Dow Chemical Co., Lockheed Martin, Northrop Grumman, Raytheon and government agencies, including the US Department of Homeland Security, the US Marines and the US Defence Intelligence Agency. The emails show Stratfor’s web of informers, pay-off structure, payment laundering techniques and psychological methods.
Obama Leak Investigations (internal use only – pls do not forward)
Released on 2012-09-10 00:00 GMT
Email-ID 1210665
Date 2010-09-21 21:38:37
From burton@stratfor.com
To secure@stratfor.com
Brennan is behind the witch hunts of investigative journalists learning
information from inside the beltway sources.
Note — There is specific tasker from the WH to go after anyone printing
materials negative to the Obama agenda (oh my.) Even the FBI is
shocked. The Wonder Boys must be in meltdown mode…
ON “COGNITIVE INFILTRATION” VERY IMPORTANT ISSUES
http://en.wikipedia.org/wiki/Cass_Sunstein
http://rationalwiki.org/wiki/Cognitive_infiltration
http://www.salon.com/2010/01/15/sunstein_2/